RANSOMWARE PREVENTION
Detect, disrupt, and disarm ransomware attacks in record time.
ThreatEye breaks the cycle of lateral movement and other key ransomware stages by detecting their signals regardless of encryption.
ThreatEye breaks the cycle of lateral movement and other key ransomware stages by detecting their signals regardless of encryption.
With instantaneous detection and response, behavioral analytics, and threat hunting capabilities, ThreatEye provides a holistic view of network traffic and user behavior, helping your SecOps team quickly identify and respond to potential ransomware attacks. By integrating with Security Information and Event Management (SIEM), SecOps centralizes threat management and correlates threat intelligence across the entire organization.
ThreatEye hunts down attackers before they can set up camp in your network. By detecting ransomware attacks in their early stages, ThreatEye enables you and your team to disrupt their plans before they disrupt yours.
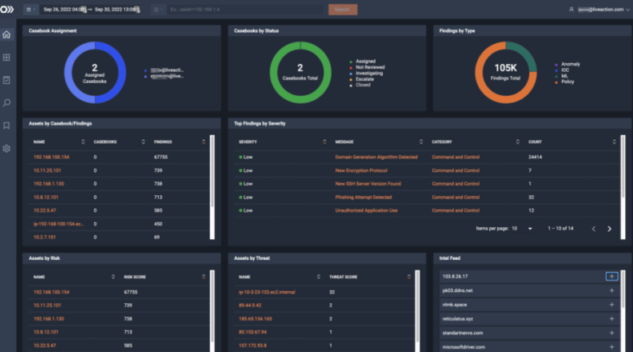
ThreatEye is always on the lookout for ransomware attacks, whether detecting a hands-on keyboard attack through packet dynamics or using an ML-powered analysis to uncover lateral movement. By analyzing over 150 packet dynamic traits, ThreatEye saves you and your team from resource-draining packet inspection.
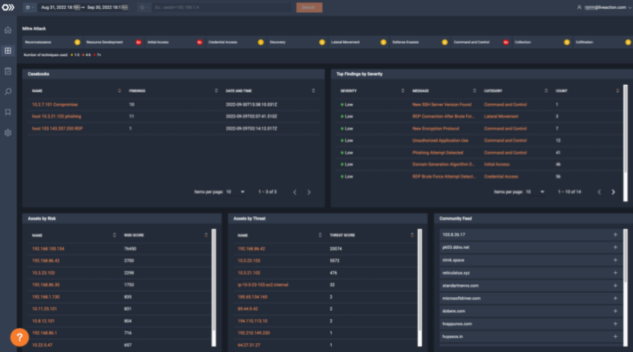
Encrypted traffic is an ideal hiding place for ransomware attackers. ThreatEye uses ML to fingerprint and baseline your network’s traffic with Encrypted Traffic Analysis (ETA) to quickly and accurately identify ransomware attacks regardless of encryption.
By combining streaming machine learning with advanced behavioral analysis, ThreatEye detects threats that other tools miss. Enriched alerts are risk-scored and Mitre ATT&CK-labeled to inform and prioritize every response.
ThreatEye’s SaaS approach works in the cloud, on-premises, and within protocols like RDP, SSH, and HTTPS, regardless of encryption, generating unmatched network visibility for even the largest enterprise networks.
ThreatEye provides comprehensive visibility into network traffic and user behavior to allow your security teams to monitor network traffic in real-time to identify potential threats and proactively prevent ransomware attacks.




Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Get to know LiveAction’s triple threat product suite.