NETWORK SECURITY
AI-Driven Network Detection and Response.
Stop playing hide and seek with threat actors. Combat advanced cyber-attacks and ransomware with AI-driven anomaly detection and predictive intelligence using ThreatEye NDR.
Stop playing hide and seek with threat actors. Combat advanced cyber-attacks and ransomware with AI-driven anomaly detection and predictive intelligence using ThreatEye NDR.

Today’s threats are so sophisticated that they can bypass legacy security tools through visibility gaps caused by cloud, mobile, and IoT adoption. More attackers are using encryption to create blind spots in your network, and your traditional NDR solution won’t be able to detect a malicious cyberattack until it’s too late.
Of organizations are challenged with detecting threats within encrypted traffic (according to Lawless Research).
The average number of days between data exfiltration and a ransomware attack.
Of enterprises say strong AI is essential to a powerful NDR solution.

46% of organizations identify network detection and response technology as most effective for identifying and responding to threats, due to the network’s vantage point across the business. Attackers seek to exploit the siloed visibility many organizations have across cloud and on-premises.
By enriching and correlating data from disparate sources, ThreatEye’s AI-driven platform uses advanced fingerprinting techniques to characterize the behavior of network assets and identify malicious activity across on-premises, cloud, and hybrid networks. Integration with LiveWire provides single-click, packet-level forensics that mean time to resolution (MTTR) and help SOC teams respond to cyber threats in real-time.
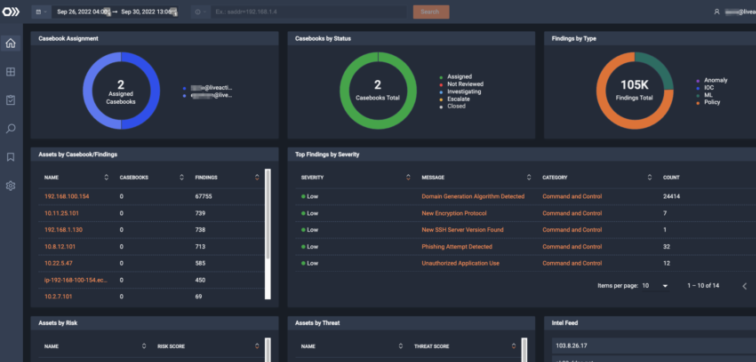
Decrypting network traffic is challenging to manage, expensive to operate, and kills network performance. ThreatEye combats cyber-attacks by applying machine learning to Deep Packet Dynamics (DPD) without decryption. This approach eliminates encryption blindness while significantly reducing operational costs and complexity. Additionally, ML-driven device discovery allows enterprises to identify IoT and rogue devices that may be compromised.
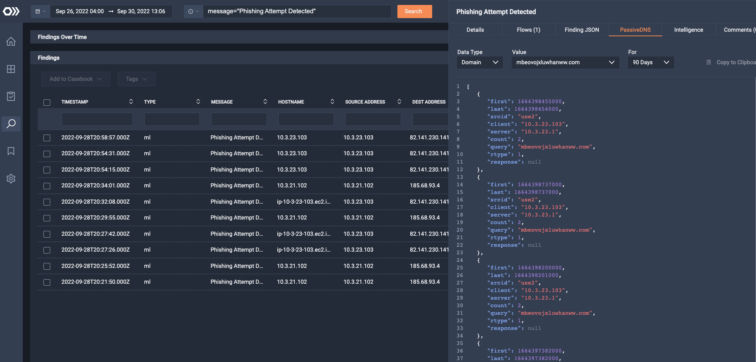
ThreatEye monitors internet-facing infrastructure by mapping malicious groups, traffic, and activity upon activation. Using this data and a multi-stage analysis pipeline, ThreatEye provides your SOC team with a cohesive data story (geography, passive DNS, MITRE ATT&CK techniques, threat intelligence, risk scores) to reduce ransomware impact by resolving incidents faster.
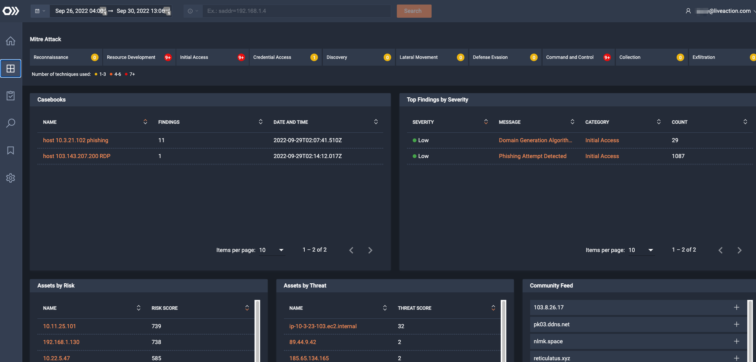
ThreatEye’s workflows and casebooks enhance SOC analyst workflows by integrating data enrichment and packet analysis into a single interface. ThreatEye enables team collaboration using casebooks that support analyst workflow stages and event tagging. This integrated approach enriches, collaborates, and alerts, reducing investigation costs and overall MTTR.
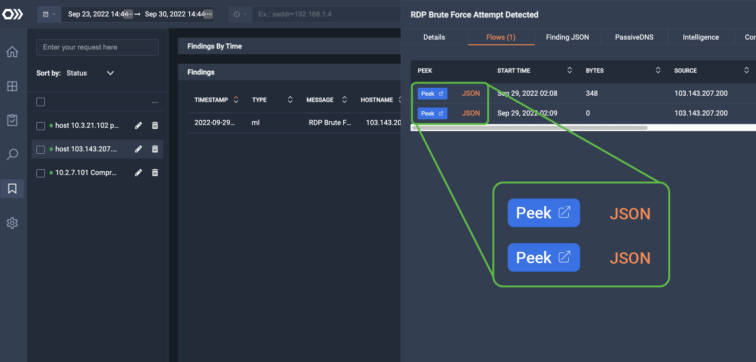
By integrating with your existing security tools, ThreatEye enhances your security defense toolset without creating more disparate environments, making it easy to streamline your security operations and get a comprehensive view of your security posture.
Get to know LiveAction’s triple threat product suite.