ENCRYPTED TRAFFIC ANALYSIS
Protect your network from hidden threat actors.
LiveAction’s encrypted traffic analytics (ETA) fingerprints, maps, and profiles your network and device behavior to protect your network without decrypting it.
LiveAction’s encrypted traffic analytics (ETA) fingerprints, maps, and profiles your network and device behavior to protect your network without decrypting it.
As more network traffic is now encrypted using Transport Layer Security (TLS) or Secure Sockets Layer (SSL), it is increasingly difficult for security teams to detect and analyze threats in this traffic. ETA uses machine learning and advanced algorithms to analyze encrypted traffic metadata and behavior and identify threats.
ThreatEye combines data collection, advanced behavioral analysis, and machine learning to analyze traffic in real-time, strictly with flow data, to provide the context security teams need.
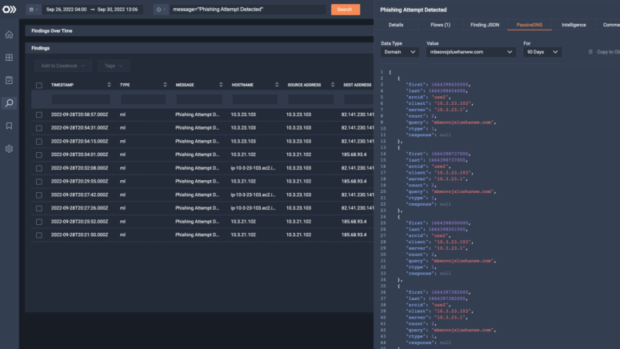
ETA identifies threats within encrypted traffic, including malware, command, and control (C&C) communications, data exfiltration, and more without decryption.
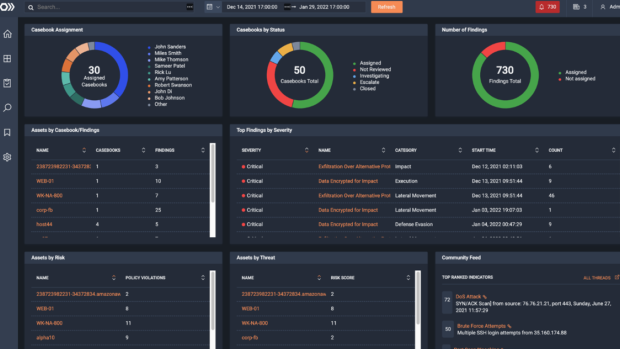
ThreatEye’s ETA can analyze any volume of encrypted traffic without impacting network speed or performance.
ThreatEye offers compliance-specific alerts and reporting to help you meet regulatory requirements for monitoring and analyzing encrypted and unencrypted network traffic.
ThreatEye identifies and alerts your security team to potential threats in real time, enabling them to respond quickly and effectively to mitigate the impact of an attack.
ThreatEye correlates and enriches encrypted traffic with details, risk scores, and MITRE ATT&CK labels to help with SOC compliance and accelerate investigation and response.




Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Get to know LiveAction’s triple threat product suite.