DEEP PACKET DYNAMICS
Defend every datapoint with deep packet dynamics.
DPD helps ThreatEye detect and block a wide range of cyber threats while minimizing false positives and improving the accuracy of threat detection.
DPD helps ThreatEye detect and block a wide range of cyber threats while minimizing false positives and improving the accuracy of threat detection.
ThreatEye’s DPD capabilities help the system analyze network traffic at the packet level, identifying hidden threats that traditional security solutions may miss. With comprehensive security coverage and a user-friendly interface, DPD helps make ThreatEye an essential tool for any organization looking to strengthen its cybersecurity defenses.
DPD captures and inspects network traffic at a granular level, analyzing the contents of individual packets in real time.
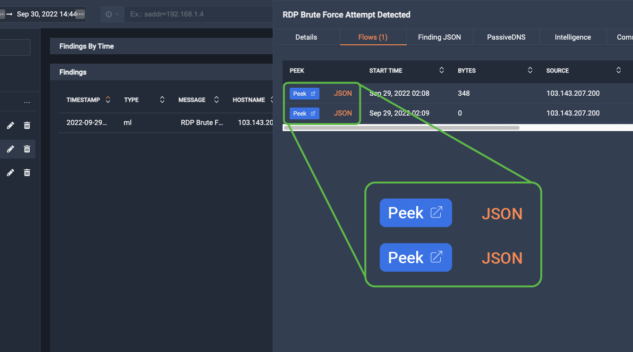
DPD allows ThreatEye to collect over 150 traits and characteristics, including producer/consumer ratio, jitter, RSTs, retransmits, sequence of packet lengths and times (SPLT), byte distributions, connection set-up time, and round-trip time.
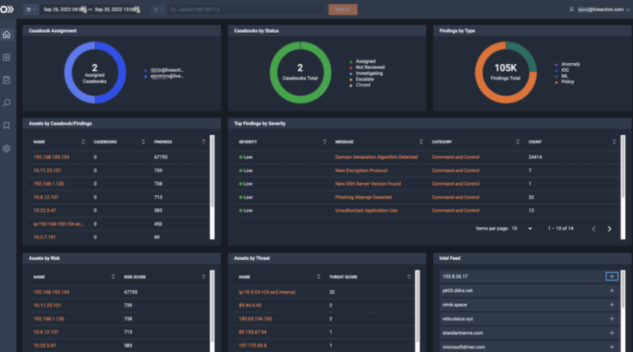
The combination of DPD with machine learning detects data exfiltration by understanding application “fingerprints” and analyzing producer-consumer ratios (PCR).
By analyzing packets as they flow through the network, ThreatEye DPD helps detect threats in real time, minimizing the impact of an attack.
By examining the contents of individual packets, DPD can distinguish between legitimate and malicious traffic in real-time with fewer false positives than traditional security solutions.
ThreatEye’s DPD technology analyzes network traffic at multiple layers, including the application layer, so that you can detect and block various cyber threats, including malware, phishing attacks, and data exfiltration.




Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Get to know LiveAction’s triple threat product suite.