NETWORK FORENSICS
ThreatEye powers network forensics.
Continuous packet capture (PCAP) with customizable retention lets you dig deep into security issues and while helping to ensure compliance.
Continuous packet capture (PCAP) with customizable retention lets you dig deep into security issues and while helping to ensure compliance.
ThreatEye enables detailed investigations of network security incidents by capturing and analyzing network traffic, performing deep packet inspection, and conducting threat-hunting activities. By storing packet history for on-demand analysis, your SecOps team can more easily identify the root cause of security incidents and prevent similar incidents from occurring in the future.
With ThreatEye, you can uncover and preserve attack evidence, confidently map attacker pathways and timelines, and fully analyze security incidents.
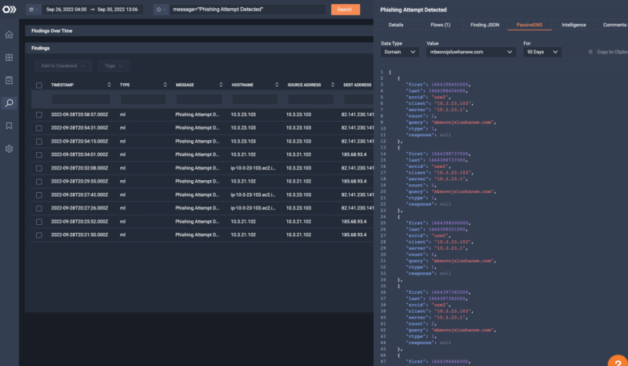
With long-term behavior baselining, ThreatEye maintains a detailed record of what is normal so attacker actions stand out. Now, investigators can confirm an attack and analyze the recorded packets to document who, what, when, where, and how.
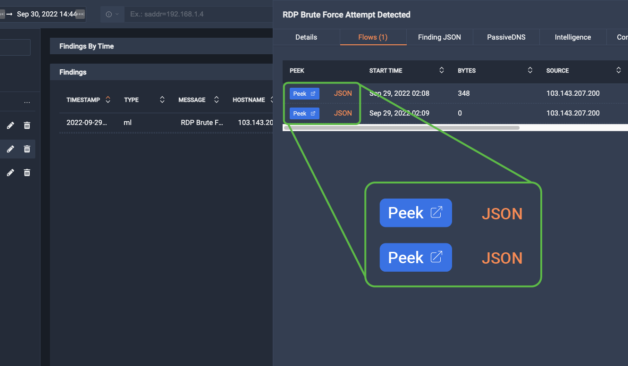
ThreatEye allows your forensic investigation team to see the forest and the trees. Go from a global alert view to extreme detail, including all packets for troubleshooting, remediation, and compliance.
ThreatEye’s Encrypted Traffic Analysis (ETA) detects and spotlights threat actor behavior, even if threats are operating within encryption.
The ThreatEye NDR workflow includes forensics to help SecOps team members learn how to detect attacks faster with tell-tale clues. This real-time exercise helps raise the skill level of your entire team.
By providing detailed audit logs, comprehensive reporting, and policy-based alerting, ThreatEye helps you comply with industry regulations and standards such as HIPAA, PCI-DSS, and GDPR.




Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Get to know LiveAction’s triple threat product suite.