NDR PLATFORM
Find attackers hiding out in your network.
ThreatEye creates unprecedented visibility into encrypted traffic, threats, and network anomalies.
ThreatEye creates unprecedented visibility into encrypted traffic, threats, and network anomalies.
Cyber defenders are struggling to detect advanced threats on the network, and the problem is getting worse. Record encryption levels are colliding with outdated tools and traditional rules-based approaches that are blind to encryption. Attackers are going undetected, and teams are burning out. ThreatEye delivers advanced attack detection across on-premises, WAN / SD-WAN, cloud, and hybrid networks.
Reduce organizational risk and prevent downtime by stopping cyber attacks before they happen.
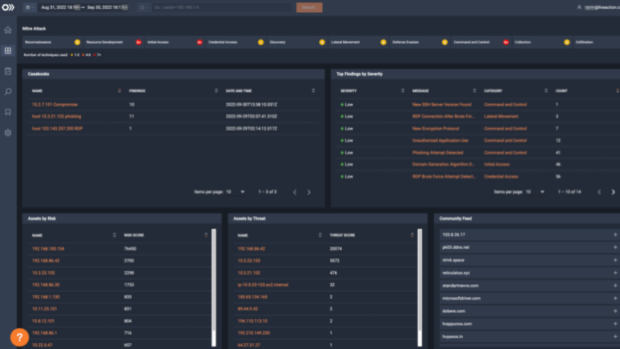
ThreatEye NDR utilizes new levels of computational power, including next-generation data collection, advanced behavioral analysis, and streaming machine learning to examine new or unusual activity to work out what is malicious and stop it.
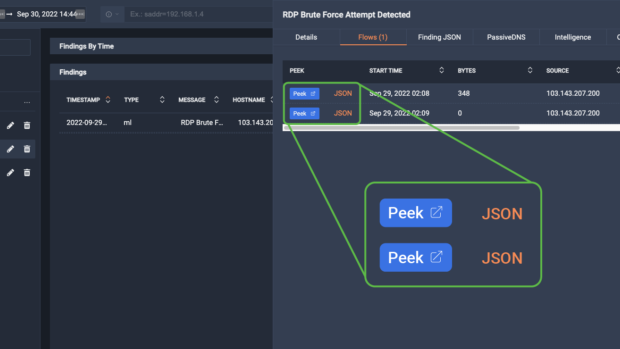
ThreatEye detects threats through Encrypted Traffic Analysis (ETA) that never requires payload inspection or costly and complex decryption techniques.
ThreatEye uses real-time machine learning to process millions of events per second, detecting lateral movement, data staging, exfiltration, phishing, insider threats and other cyber attacks with a single pass over the data stream.
Integrate with your existing security tools, including SIEMs, SOAR, and Threat Intelligence. LiveAction’s highly configurable workflow automation helps your SecOps team respond swiftly to security threats.
Alert fatigue is real! ThreatEye creates enriched alerts that are risk-scored and MITRE ATT&CK labeled. With a click, analysts can dive down to the packet level. Smarter alerts inform your response and reduce team frustration.




Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
Get to know LiveAction’s triple threat product suite.