Contents
TLS 1.3 is a cybersecurity acronym for Transport Layer Security, version 1.3.
Transport Layer Security is the most used method of encrypting internet traffic.
You are using this protocol if you see a lock symbol in your internet browser bar, and if you reveal the complete web address, you should see HTTPS: as well. The ‘s’ stands for secure. Here are two examples:


Let’s explore why TLS exists, its history, and the growing difficulty TLS 1.3 creates for cybersecurity professionals.
Why do we need Transport Layer Security?
Why does Transport Layer Security matter? And how exactly do you define it?
One of our favorite definitions cuts through jargon and explains the value of TLS in simple terms.
“Transport Layer Security (TLS) encrypts data sent over the Internet to ensure that eavesdroppers and hackers are unable to see what you transmit, which is particularly useful for private and sensitive information such as passwords, credit card numbers, and personal correspondence.” –Internetsociety.org
The Internet Engineering Task Force manages and updates the protocol. Watch this video for an explanation:
The history of TLS: how did we get to version 1.3?
If you used a web browser called Netscape Navigator in the mid-1990s, you are part of encryption history.
Netscape realized sending data over the internet was unsafe. Web traffic traveled the world as plain text. This opened the door for hackers to read, intercept, or impersonate data and connections.
In response, Netscape introduced an encryption protocol called Secure Socket Layer (SSL). Netscape Navigator protected users with SSL, which established secure links between networked computers.
That was the start.
And the European Union Agency for Cybersecurity (ENISA) chronicles what happened next.
“SSL 2.0 was designed in 1995. However, due to vulnerabilities, a more secure SSL 3.0 was released a year later. It was widely used until 2014 – when a major security vulnerability found by Google security team. TLS emerged out of SSL technology and has overshadowed it.”
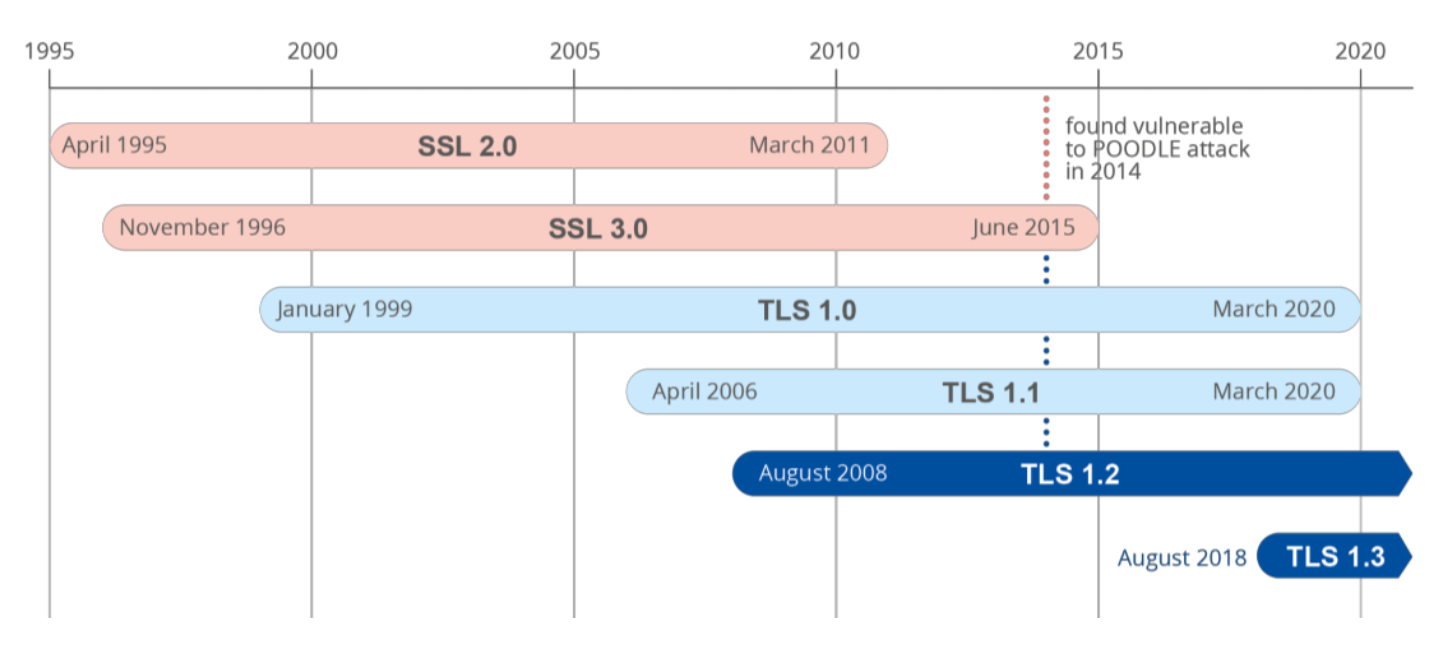
Right now, rapid deployment of TLS 1.3 is underway.
How does TLS 1.3 work and what does it accomplish?
Version 1.3 of transport layer security increases your internet privacy to a new level. It uses a high-speed digital handshake and exchanges secret keys to accomplish several things:
- Confidentiality of a connection: prevents anyone from reading the contents
- Authentication: verifies the identity of the parties communicating
- Message Integrity: verifies that nothing modifies a message between sender & receiver
“TLS 1.3 also enables forward secrecy by default which means that the compromise of long-term secrets used in the protocol does not allow the decryption of data communicated while those long-term secrets were in use. As a result, current communications will remain secure even if future communications are compromised.”
More robust encryption is great for privacy and a problem for network defenders. Encryption blinds cybersecurity teams and blocks the detection of malicious traffic.
How does TLS 1.3 impact cybersecurity?
While TLS 1.3 improves privacy, it also makes security investigations harder.
Version 1.3 blocks most decryption. As a result, a “break and inspect” approach to network security is much less effective. The “break and inspect” (TLSI) approach involves decrypting network data to inspect it for threats. Now, however, there is very little you can break or decrypt. And traditional DLP and IDP tools are also blinded by encryption.
This is why ENISA issued a special report explaining the challenges created by TLS 1.3 and what to do about them:

“TLS 1.3 has started to be used and deployed massively…the drawback is that the certificate is now encrypted inside the HTTPS traffic. Hence feature extraction from certificates, which was a very useful way of identifying malicious traffic, can no longer be used.
So, while TLS 1.3 is a step in the right direction for the Internet and it is very good to use from a user perspective, it invalidates existing techniques making detection of malicious behaviour harder.”
The solution to this problem is Encrypted Traffic Analysis (ETA). It looks at the behavior of network traffic, devices, and assets to find anomalies.
ETA does not decrypt network traffic, however, it does detect advanced threats across your entire network from core, to edge, to cloud.
