Encryption is a data security practice that converts normal, readable information into an unintelligible cypher. Once network traffic is encrypted, it can only be accessed by authorized users with a key, or by advanced encryption practices that can decode cyphertext. This process allows organizations to safely move confidential and sensitive information around without exposing it to bad actors.
Contents
What is lateral movement across a computer network?
It’s an important stage of modern cyberattacks, including ransomware.
Let’s look at what lateral movement is, how attackers use it, and explore the way strategic IT and cybersecurity teams can detect it.
What is the definition of lateral movement?
The MITRE ATT&CK framework defines the term like this:
“Lateral Movement consists of techniques that adversaries use to enter and control remote systems on a network. Following through on their primary objective often requires exploring the network to find their target and subsequently gaining access to it. Reaching their objective often involves pivoting through multiple systems and accounts to gain.”
In the case of the 2021 Colonial pipeline cyberattack, a ransomware group accessed the company’s network through a VPN account that the company no longer used. Then they looked around for things of value to target.
At that point, the attackers began the lateral movement part of the attack. In many cases, this occurs over a span of weeks or even months.
What are the stages of lateral movement?
According to Thomas Pore of LiveAction’s ThreatEye team, lateral movement is generally outside the interest of the enterprise. And he sees cyber threat actors utilize it in the following stages:
- Discovery – what does the organization have of value on the network?
- Access – what kind of credentials are needed to reach the data & systems of value?
- Penetration – using acquired/stolen credentials and pathways to get deeper into the network
- Exploitation – using the network penetration to steal/encrypt data or disrupt net ops
- Repeat these steps
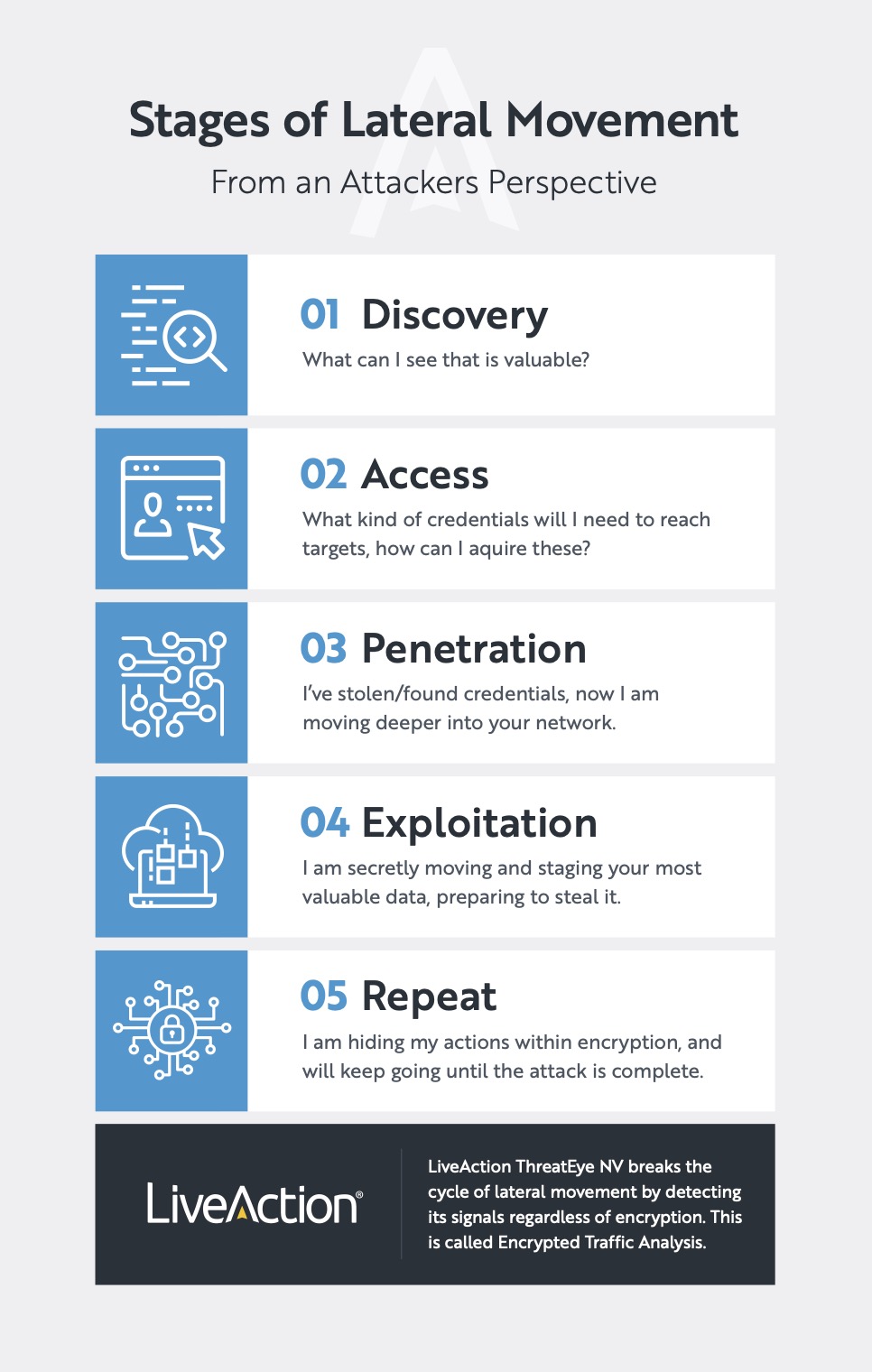
These repeated cycles of lateral movement set the stage for a successful conclusion to the cyberattack. And they often go undetected until it is too late. Threat actors are taking advantage of the fact that about 90% of network traffic is encrypted and often uninspected.
Security teams without the visibility and tools to detect unusual behavior, regardless of encryption, are at a serious disadvantage here. You cannot stop what you cannot detect.
Some technical examples of lateral movement
For our technical readers, here are some details on lateral movement and detection from LiveAction’s Thomas Pore.
“Lateral movement detection is about identifying conditions where an endpoint attempts to extend its local associations outside its normal collection of assets. It typically involves unique network behaviors, such as interactive sessions, stepping stones, data migration, data concentration and exfiltration.”
Below is a list of definitions from his experience. There is a caveat here: whether these apply to your environment will depend on your security strategy or architecture.
- Host ‘A’ performs a port scan against Host ‘B’
- Then a bi-directional connection is established against one of the open scanned ports
- 2 Hosts interacting within the same DHCP subnet“Traditionally DHCP is used for user environments, less so for server infrastructure. Servers tend to be configured with Static IP addresses. In a perfect world, you wouldn’t want to connect with another host in a DHCP environment, say Starbucks or at a hotel. In the enterprise world, this should be a red-flag .”
- IPAM Rule Enforcement
- In large organizations, IP Address Management (IPAM) is challenging, so they typically use an IPAM tool to define and track IP space. As part of this, having the ability to define who is allow or not allowed to communicate with one another becomes important.
And Pore also touched on more sophisticated attacks. “There are advanced lateral movement attacks using Cobalt Strike and similar post-exploitation tools.” Cobalt strike is designed for cybersecurity researchers and professionals to test IT networks for security holes. Now attackers use these tools as well.
“This is where advanced behavioral analysis of host (asset) baselines becomes important. Regardless of the protocol attackers use to establish a connection from one host to another, understanding the relationship of those hosts and the probability of that connection being established is a great way to detect anomalies.”
Concluding thoughts on lateral movement
In the case of Colonial Pipeline, attackers completed their lateral movement, encrypted the company’s billing system, and removed 100GB of data. They then demanded a ransom and the company paid.
This article is a quick share resource for when you need to explain what lateral movement is, what the various stages of lateral movement are, and how this type of movement enables cyberattacks.
About LiveAction
LiveAction provides unmatched visibility into network and application performance from a single pane of glass. This gives enterprises confidence that the network is meeting business objectives, offers IT administrators full visibility for better decision-making, and reduces the overall cost of operations. By unifying and simplifying the collection, correlation and presentation of network and application data, LiveAction empowers network and security professionals to proactively and quickly identify, troubleshoot, and resolve issues across increasingly large and complex networks. To learn more and see how LiveAction delivers unmatched network visibility and security, visit https://www.liveaction.com.
