
A lawsuit targeting SolarWinds is sending chills down the spine of Chief Information Security Officers. And the breach behind it is also changing how organizations approach cybersecurity.
Let’s look at two things that are shifting in the time since the SUNBURST cyberattack.
Judge: Lawsuit Against CISO Can Proceed
An ongoing investor lawsuit is part of the fallout from the SolarWinds Orion/SUNBURST cyberattack. The suit specifically names CISO Tim Brown (among others) and a judge now says it can proceed.
From SC Media:
“On Brown, who was vice president of security architecture at SolarWinds and was promoted to chief information security officer following the breach, the court ruled that both his position overseeing cybersecurity at the company and his public statements in media interviews endorsing SolarWinds cybersecurity posture made him and SolarWinds liable.”
Cyber and Privacy Law Attorney Rebecca Rakoski, of XPAN Law Partners, says the C-suite needs to watch this case closely, as a clue about litigation CISOs might face in future breaches. That is one shift.
And this particular attack also spurred something else: increased adoption of Network Detection and Response (NDR) platforms. It was a pivot point in how forward-looking organizations approach cybersecurity.
The SolarWinds SUNBURST security incident is another event that generated more interest
in NDR. -Gartner
Why does SUNBURST mean more interest in NDR?
In the case of the Orion/SUNBURST attack, malicious actors compromised and hid within legitimate, signed, SolarWinds updates. The company’s customers accepted these updates as legitimate and that gave nation-state actors potential access to each compromised customer.
For the security community, it was an eye-opening reality about the sophistication and scope of third-party risk. Despite considerable attention to this topic, the risk was even greater than many believed.
So if attackers find their way onto your network through a trusted partner or a trusted employee’s compromised account, will you know? Can you detect it, even if it is hidden within encryption?
These are the questions organizations asked after SUNBURST. Those adopting Network Detection and Response platforms can answer yes to these questions with a higher degree of confidence.
This is why NDR adoption is growing rapidly. It gives you the ability and visibility to detect an attack in your environment, respond, and stop it-before attack completion.
NDR: How Does It Work?
A Network Detection and Response (NDR) platform learns what is normal network behavior, baselines this activity, then correlates things happening right now, and applies machine learning. This analysis allows NDR to see what is unusual or malicious so you can uncover attacks in progress and stop them.
Most traditional approaches like DLP, IDS, and others, cannot see this activity because it is hidden within encryption. In fact, attackers delivered 91.5% of malware within encrypted traffic during Q2 of 2021.
NDR: What About Visibility Within Encryption?
The LiveAction NDR platform, ThreatEye, uses a uniquely powerful approach called Encrypted Traffic Analysis (ETA). This process removes encryption as a barrier to investigation. It looks at long-term behaviors (Deep Packet Dynamics), analyzed by AI-backed machine learning. The result is real-time cryptanalysis for your environment.
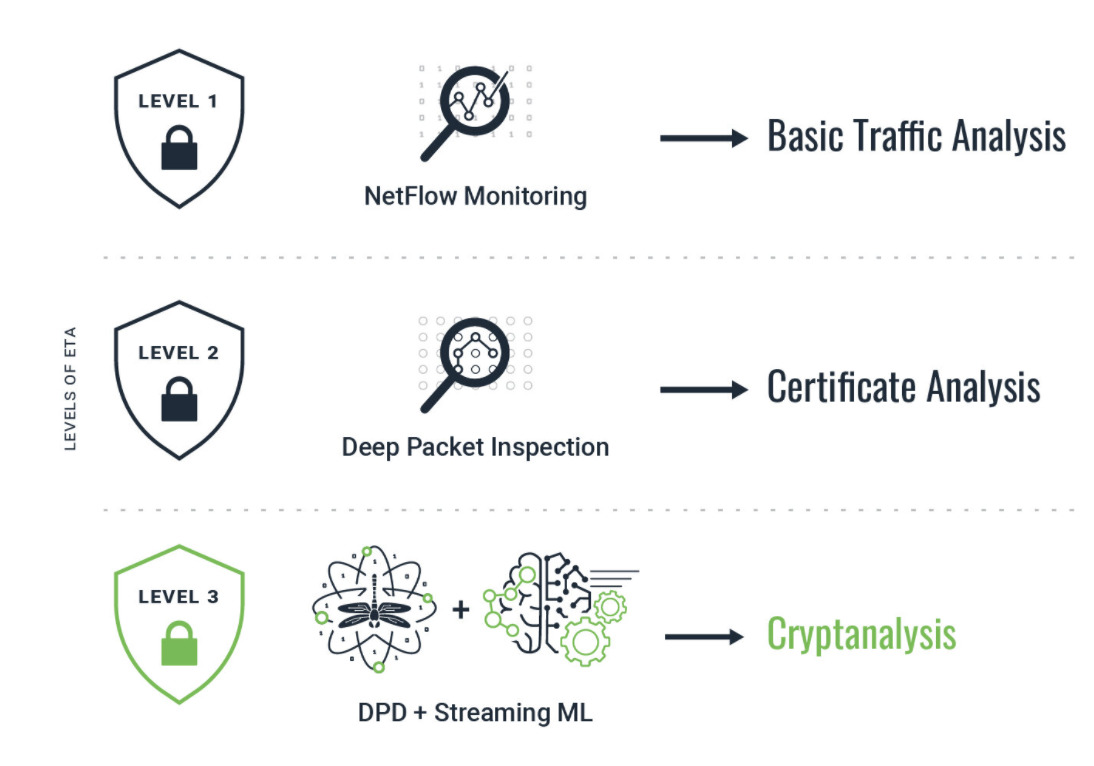
And surprisingly, there is no need for packet inspection or expensive and complicated decryption tools that other NDR platforms require.
ThreatEye also creates automated, enriched alerts to simplify response and reduce SOC team burnout. Alerts are risk-scored and MITRE ATT&CK labeled so your team will easily know which alerts matter.
Interactive: Network Detection and Response
Check out our interactive feature, Anatomy of a Ransomware Attack, for how the ThreatEye NDR platform will help you detect and stop an attack that is already in your environment. You will see how the platform turns data and analysis, into action.
NDR also supports forensics and hunting. And it can be an important part of your ZeroTrust strategy, as well.
Network Detection and Response is a powerful and proven approach to reducing cyber risk for your organization.
And it is also one of the significant pivots within security following the SUNBURST cyberattack.


