
Traditional Packet Capture
To understand why intelligent packet capture is such a powerful advantage we need to first understand what happens in traditional packet capture.
Packet capture uses a TAP or Span port (aka mirror port) to intercept data packets traveling across the network.
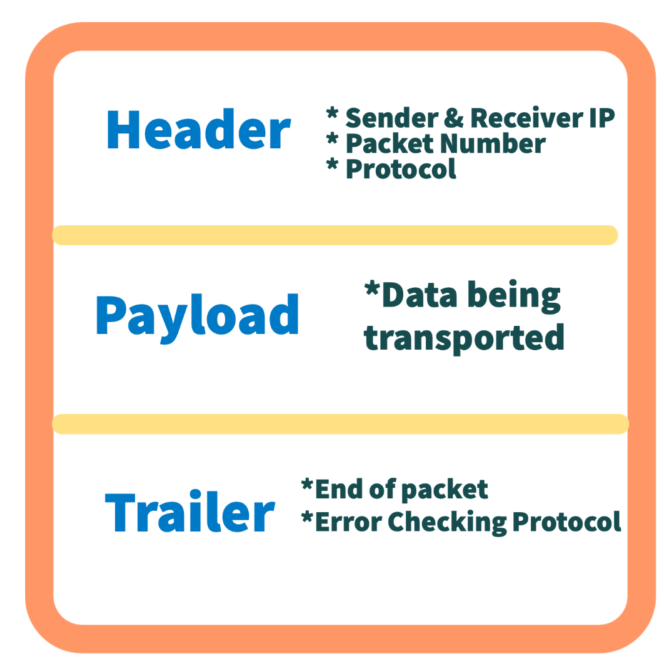
The data packets are made up of three layers, header, payload, and trailer. The payload and trailer are the data portion of the message and the header has details about that data. Packet capture is a duplicate snapshot of the entire packet. An individual packet can hold anywhere from 1000 to 1500 bytes of information.
Note: 1500 bytes is the MTU (maximum transmission unit) set by the ethernet frame, but can be higher with jumbo frames
Packet capture’s value is in allowing organizations to pinpoint exactly what is causing network disruption and are used to identify performance failures and security concerns.
Enter Intelligent Packet Capture
Intelligent packet capture slices off the payload and trailer and captures only the most relevant parts of the packet that reveal critical investigative data.
The header has all of the information to identify the data in the file. It’s loaded with details.
- Source and destination IP Address
- Exact length of the packet in bytes
- ToS (Type of Service) for routing priority
- Protocol
- Flags for troubleshooting connection state
- ex: “SYN”, “FIN” “ACK”
- Time to live
- Header checksum
- Version
Why Move Away From Traditional Packet Capture?
Simply put… traditional packet capture is not sustainable in modern networks.
The average traffic volume has doubled if not tripled for organizations in the last 5 years with the rise of The Gig Economy.
According to IBM, 90% of the world’s data has been produced within the last two years.
What is causing this?
- Increase in network applications
- Increase in network complexity
- several redundant paths for data
- private hybrid cloud or multi-cloud networks
- Rise in digital-first organizations working completely online post pandemic
Why is this a problem?
Storage and ability to retain data.
The more data analyzed, the less storage and retention time is available to an organization. This is problematic when it comes to forensic research or post-mortem investigations of network disruptions or attacks.
The cost of storage is also a consideration and eating up a significant piece of the pie for many organizations.
According to a study by McKinsey & Company, industry spending on data-related costs increased by nearly 50% between 2019 – 21 compared with 2015 – 18
Why Intelligent Packet Capture Works
Storage of only crucial packet information found in the header jumps the 1500 byte possibility down to a range of 20-24 bytes per packet.
This frees up space and increases the length of data retention for better historical threat analysis. This is critical because we are seeing longer incubation periods for attacks.
The industry average to detect a breach is 212 days after initial access
Here’s one example that will be familiar to you. The SUNBURST attack that infected SolarWinds and countless of their clients was executed after 14 months of undetected compromise and threat actor access within their systems. The only way to travel back 14 months to understand where the initial vulnerability and access point occurred, you need to have the data available to audit.
Intelligent packet capture is used to empower both NetOps and SecOps. Both teams benefit from the information. SecOps teams receive risk and threat information and NetOps teams receive server and client-side latency and application performance information.
Why People Still Use Traditional Packet Capture
The main reason organizations continue with the resource-intensive traditional packet capture is because of encrypted traffic.
With close to 90% of traffic being encrypted today, people are holding onto the payload for decryption.
This is where Intelligent Packet Capture and Encrypted Traffic Analysis (ETA) fit perfectly together. ETA allows you to determine the danger of the packet contents without having to decrypt them. If you are not decrypting the packet, there is no need to capture the payload.
Using ThreatEye ETA combined with LiveWire’s Intelligent Packet Capture frees up significant disk space for longer retention and reduces rack space in data centers.
ThreatEye by LiveAction is an ETA platform that uses AI for packet metadata extraction. Our tool is built off of deep packet dynamics to scan each packet for 150 network traits and characteristics that determine whether the packet is malicious or benign.
About LiveAction
LiveAction provides unmatched visibility into network and application performance from a single pane of glass. This gives enterprises confidence that the network is meeting business objectives, offers IT administrators full visibility for better decision-making, and reduces the overall cost of operations. By unifying and simplifying the collection, correlation and presentation of network and application data, LiveAction empowers network and security professionals to proactively and quickly identify, troubleshoot, and resolve issues across increasingly large and complex networks. To learn more and see how LiveAction delivers unmatched network visibility and security, visit https://www.liveaction.com.


