Request 30-Day ThreatEye Trial
Getting Started
Fill out the form above and you’re on your way to discovering what network intelligence is all about.
VIP Support
Our approach is a little different and we want to start you off right. Spend 30 minutes with one of our highly knowledgeable on-boarding specialists to get you up and running.
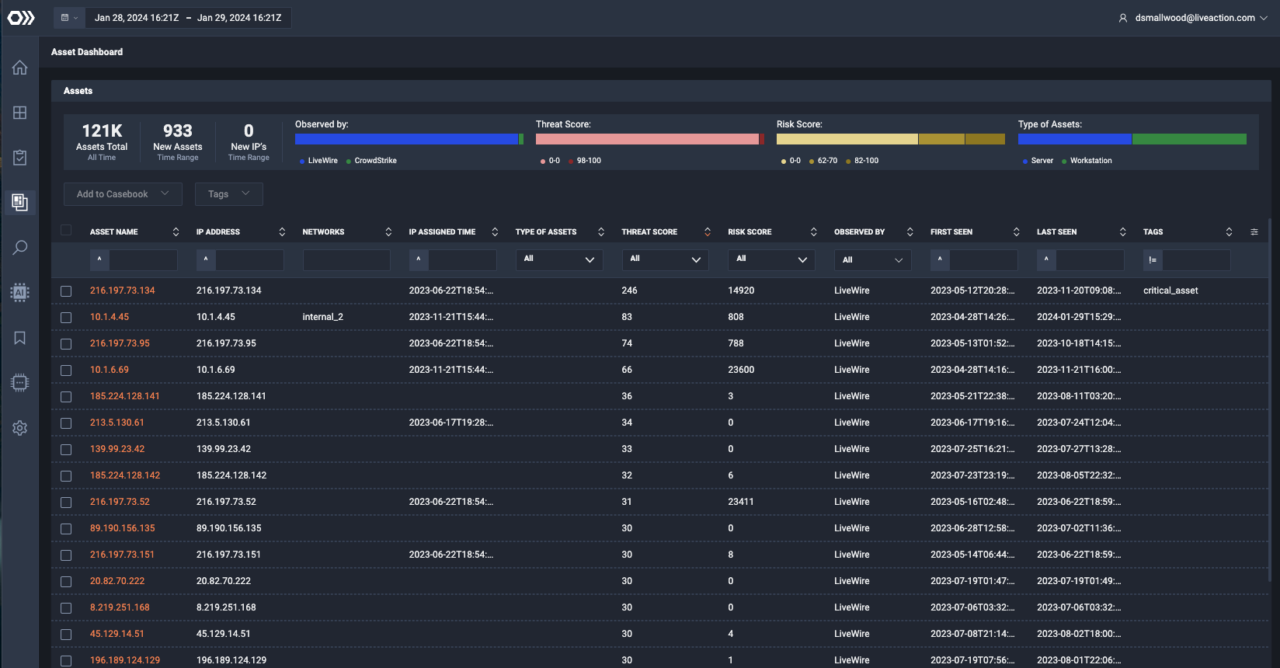
In this trial, you’ll be able to leverage AI-driven network detection and response behavioral analytics.
Encrypted Traffic Analysis
Uncover cyber threats, without decryption, by ingesting flow data from LiveWire to identify real-time cyber threats.
Behavior Analytics
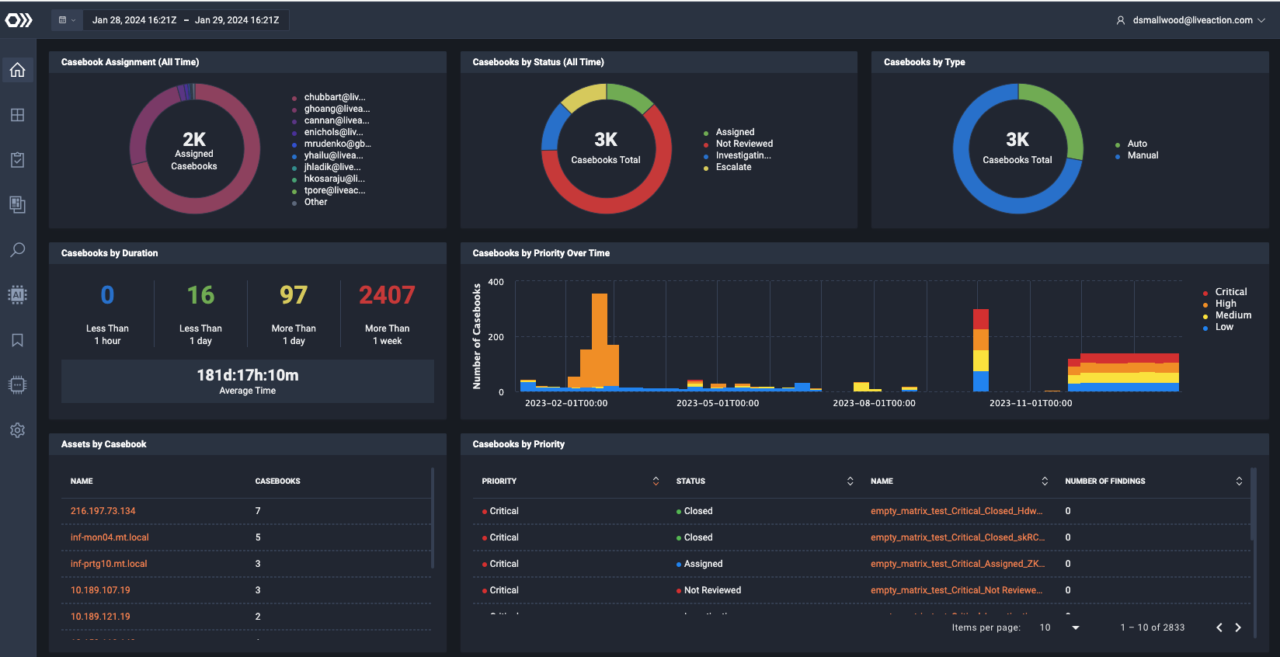
Examine network traffic traits and characteristics with ML/AI-based analysis across the largest, most complex government and enterprise networks.
Anomaly Detection
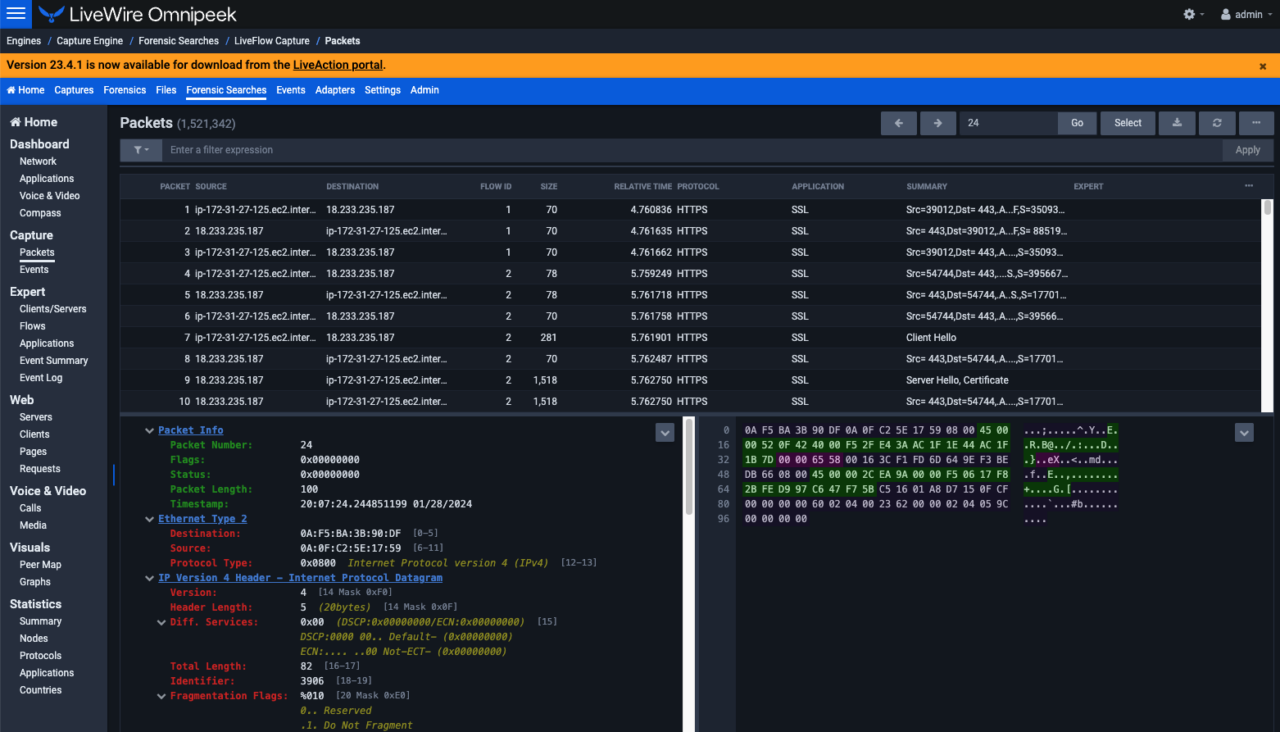
ThreatEye’s Deep Packet Dynamics is agnostic to packet contents and is used to create a fingerprint of network flows for profiling and anomaly detection.
LiveAction has the widest range of functionality, best methods of storage and visualization of any of the tools out there.
– Network Engineer
LiveAction gives us the same level of visibility we had for our physical network—but for our virtual infrastructure.
– Chief Information Officer
LiveAction meets all my specific technical needs and has always been there for us as a true partner.
– Director, Network Engineering